1 To comply with local laws regulations Eg. A Compromise Assessment allows an organisation to identify ongoing or past attacker activity in their ecosystem.
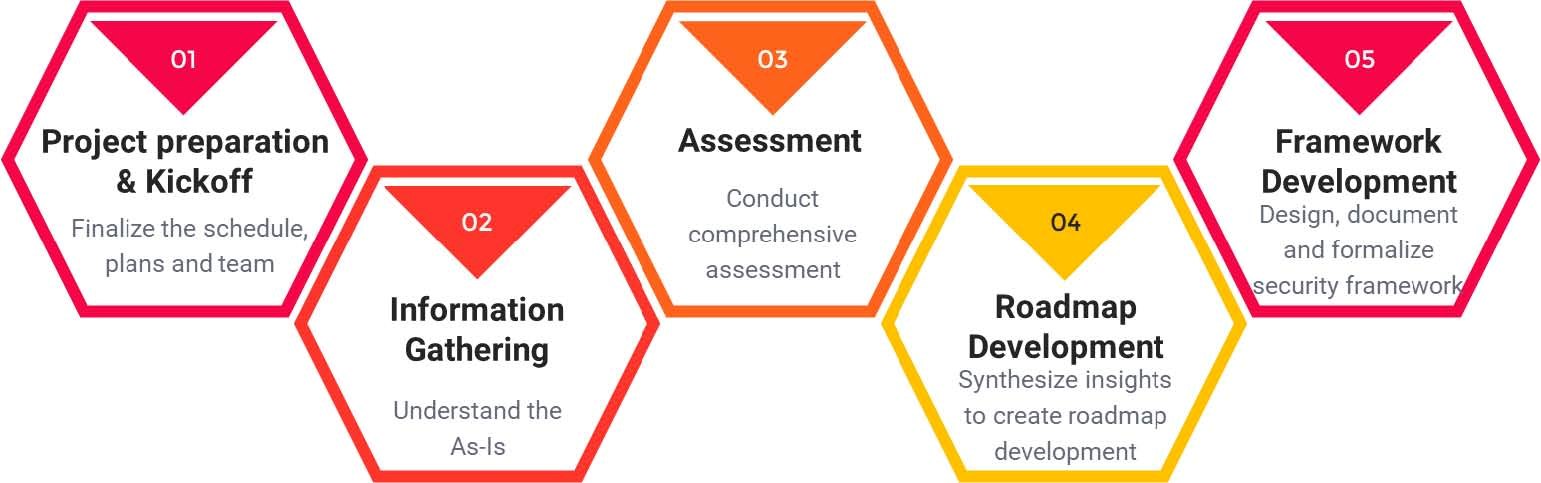
Risk Management In Technology Ec Council Global Services Egs
For example network applications may use more bandwidth than usual to send and receive traffic maybe to an obfuscated unsecured site.

. A Compromise Assessment will help an organisation by identifying current or past breaches risk assess by identifying weaknesses in security architecture identifying vulnerabilities and also flagging any regulatory or compliance. Usually there are a few reasons companies do a Compromise Assessment. A Compromise Assessment is a discipline used to identify compromised systems and derive appropriate actions based on the evidence.
A compromise assessment will provide visibility into whether there is an active compromise or a compromise in the past in that organization Ledzian says in an interview with Information Security. The Impact of Assessment. 2 To identify the presence of any security breaches.
Compromise Assessment NetAssist conducts survey of a network and its devices to discover unknown security breaches malware and signs of unauthorized access. Although different cybersecurity services follow different methods to conduct a penetration test all of them more or less come down to the same three phases. The intent of the comprehensive assessment is to answer the critical question.
This is the biggest myth about Compromise Assessment. The lab is to provide cybersecurity testing and certifications to. Bank Negara of Malaysias Risk Management in Technology.
The approach is designed to be light-touch with simple and temporary monitoring installations. We will seeks to find attackers who are currently in the environment or that have been active in the recent past. Mandiant Compromise Assessment combines extensive experience responding to intrusions carried out by advanced threat actors industry-leading threat intelligence and technology.
To seek the evidence of possible risks a Compromise Assessment will be running on detecting indicators of compromise IoC and correlating them with hard data. Compromise Assessment Identify if you are being or have been attacked. Compromise Assessment is not just about deploying another brand of EDR Scanner.
Our threat-informed approach finds historical and ongoing indicators of compromise so you. A Compromise Assessment Test is a hunting test for suspicious activities on every layer of the suspected network to detect unknown security breaches malware and signs of unauthorized access. Compromise Assessment Discover potential compromises understand the impact and get mitigation recommendations by engaging with our experts.
This helps you identify your ongoing or past intrusions assess risk by identifying weaknesses in your security architecture vulnerabilities improper usage or policy. Ideal compromise assessment leverages best-of-breed cyber threat hunting tools capable of quickly identifying and reporting suspicious activity in turn providing IT the data it needs to act. Penetration Tests and Vulnerability Assessments only tell you if your network can be hacked.
TÜV Austria Cybersecurity Lab is established in Malaysia as a joint venture between TÜV Austria and LGMS. This means that systems must be scanned and assessed manually and the scanner used does not intervene to take active action against identified potentially. A compromise assessment is composed of 4 key steps.
Onboarding and Network NormalizationAfter assessing an organizations security posture through Pandarecon we deploy SentinelOnes next-generation Singularity platform to gather security logs and data for two weeks. Compromise Assessment Firmus 2020-06-14T1449110800. Using Deloittes Cyber Compromise Assessment CCA on your estate will help identify if there is a current or indicators of a past compromise of your network - utilising the latest threat intelligence and detection techniques.
Singapore Vigilant Asia Cybersecurity Pte Ltd. Understanding when we are breached and resolving it should be the top priority. 13 For details of the Banks macroeconomic outlook refer to the BNM Quarterly Bulletin 2Q 2020.
It takes organizations an average of 191 days to identify a data breach. This creates a baseline of behavior gives us a detailed view of the. Attack Phase TargetingExploiting.
In an increasingly complex and dynamic threat landscape now more than ever organizations need to understand the. Key loggers or credential-stealing malware may. What you dont know but urgently need to find out now is if Threat Actors have already.
This requires both the sheer throughput to complete assessments in days rather than weeks and the ability to actively scan all network endpoints for suspicious behavior. It is an evaluative manual and passive discipline. Post-Attack Phase Documenting and Reporting.
Horangi Compromise Assessment will tell you if your network has already been compromised with Threat Actors lying dormant waiting for the right time to strike. Malaysia Vigilant Asia M Sdn Bhd 1255978-D No 3 Jalan Astaka U882 Bukit Jelutong 40150 Shah Alam Selangor Malaysia. Of Stress Testing in Malaysia in the BNM Financial Stability and Payment Systems Report 2012.
A Compromise Assessment CA is a comprehensive automated evidence-based analysis and evaluation of an organizations entire digital environment and cybersecurity posture and is designed to. Compromise assessments are high-level investigations where skilled teams utilize advanced tools to dig more deeply into their environment to identify ongoing or past attacker activity in addition to identifying existing weaknesses in controls and practices. 14 Used by banks to inform the setting of internal capital targets as part of the Internal Capital Adequacy Assessment Process ICAAP.
Pre-attack Phase Research Information Gathering Phase 2.
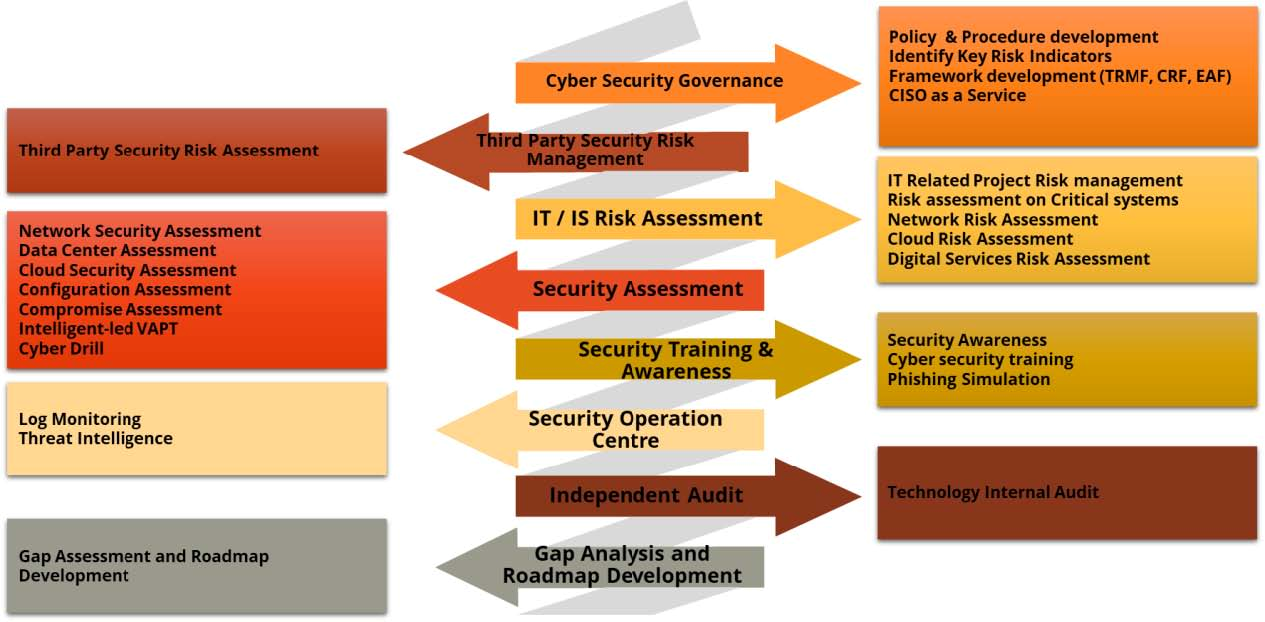
Risk Management In Technology Ec Council Global Services Egs

Compromise Assessment Cybereason Assessments

Compromise Assessment 7 Things You Should Know Lgms Blog

Compromise Assessment 7 Things You Should Know Lgms Blog

Compromise Assessment Condition Zebra Cyber Security Company Malaysia

Technical Risk Assessment Data Sheet Crowdstrike

Compromise Assessment Condition Zebra Cyber Security Company Malaysia

Compromise Assessment 7 Things You Should Know Lgms Blog
![]()
Compromise Assessment Cybereason Assessments

Cyber Compromise Assessment Deloitte China Risk Advisory

Compromise Assessment Malaysia Uncover Hidden Security Risks Firmus

Compromise Assessment 7 Things You Should Know Lgms Blog
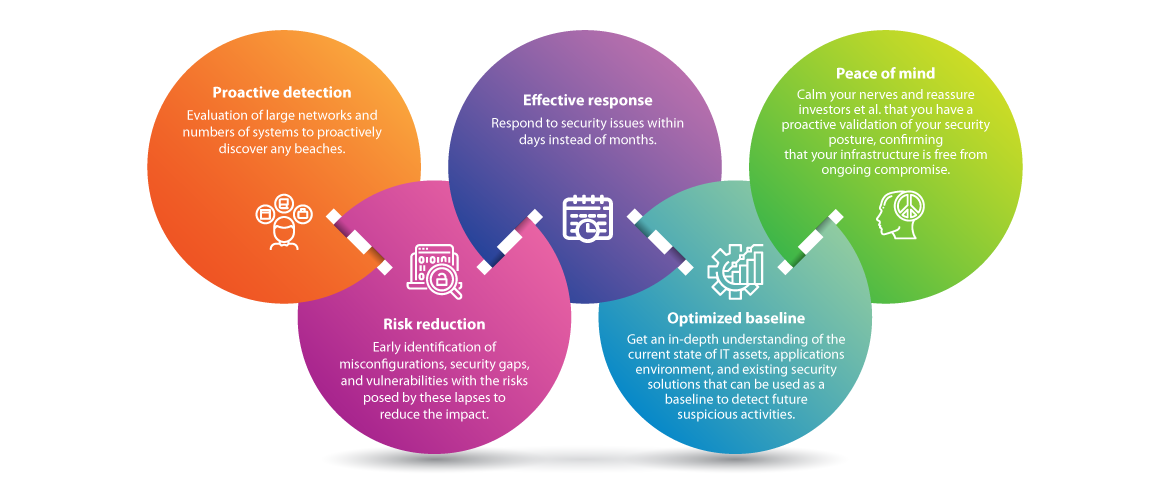
Compromise Assessment Ec Council Global Services Egs

Indicators Of Compromise Definition

Compromise Assessment Ec Council Global Services Egs




